The idea of this blog post was born after reading an italian article about CTB-Locker. I don’t remember where I read it, but a single phrase caught my attention. It sounds like: “the malware proves that it’s able to decrypt some files, so the keys are saved somewhere”. I received a CTB-Locker sample on my personal mail box, so I decided to give it a try, just to satisfy my curiosity.
The post is based on a reversing session over a single file (810d51f6a5b4f8396ecf9407e427b999b316ecc28d53a759401143442b1a5cf8), but I think you can apply the general scheme to another sample of the same family.
Basically, all the information required by the malware are saved inside two distinct files: HelpFile and HiddenInfo. You won’t find these two files on an infected machine because these are confidential names I used while I was reversing the malware, the real names are generated following a precise scheme. To understand how the real names are generated I have to introduce the very first crypto scheme used by the malware, this is very important for the entire encryption/decryption process.
Everything starts from the value of the key:
HKLM\SOFTWARE\Microsoft\Cryptography\MachineGuid
The malware removes ‘–‘, converting everything into a sequence of 32 bytes (i.e. “463109ab-151a-463a-348e-79bbc9369cbd” becomes b’\x46\x31\x09\xab\x15\x1a\x46\x3a\x34\x8e\x79\xbb\xc9\x36\x9c\xbd’). Then SHA256 is applied:
CoreHash = SHA256(converted_MachineGUID)
CoreHash is composed by 8 dwords and each one of them is used for a specific job, for this blog post I’ll focus on the first and fourth dwords.
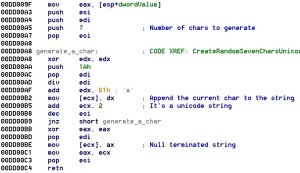
The HelpFile real name is constructed calling the next function with the CoreHash’s fourth dword as input:
The real name is 7 bytes long and every single char is built after two simple math operations. HelpFile has “.html” extension and it’s used to show ransom info to the infected user, it’s just like a *FAQ* page on how to restore all the compromised files. The message is available in four languages: de, it, nl and en.
This is the it version, but you can easily identify the server addresses, the tor access and the public keys. The last part of the file contains the list of the compromised files. Well… interesting but the keys I was searching for are not here!
The real name of HiddenInfo is obtained in the same way, but this time the parameter passed to the routine is the first dword of CoreHash. The file is without extension, it’s an hidden file and there are 0x28E meaningless bytes inside.
HiddenInfo is very important and it has a specific format, but everything is visible after a quite simple decryption process.
The malware uses AES:
DD1163 mov ecx, 0EF93F8h ; Decryption key: CoreHash DD1168 call AESExpandKey ... DD1181 lea edi, [esi+27Eh] ; Decryption starts from block at offset 0x27E DD1187 Decrypt_32_bytes_block: DD1187 lea eax, [ebp+expandedKey] DD118D push eax DD118E push edi ; Block to decrypt DD118F push edi ; Output buffer (bytes are replaced) DD1190 call AESDecrypt DD1195 add esp, 0Ch DD1198 dec [ebp+arg_0] ; initial value is 0x27E DD119B dec edi ; Update the pointer to the block to decrypt DD119C cmp [ebp+arg_0], 0 DD11A0 jge Decrypt_32_bytes_block
I told you it’s simple.
This file is important for the malware, and to be sure of its integrity the malware uses a checksum algo over the first 0x28C decrypted bytes:
DD11A2 push 28Ch ; Number of bytes used for the checksum DD11A7 mov ecx, esi ; Sequence of 0x28E decrypted bytes DD11A9 call Checksum ; ax gets the final value DD11AE pop ecx DD11AF pop edi DD11B0 cmp [esi+28Ch], ax ; Is checksum ok? DD11B7 jnz short corrupted_file
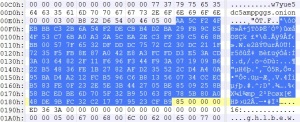
The value from the last two bytes of HiddenInfo is the valid checksum value, it was calculated during the encryption process. If the checksum is ok, at the end of the procedure you have the clean and readable HiddenInfo file. It’s full of hidden info, but in this case I’m interested in a minor part of the file only. Let’s start with this interesting block of 160 bytes:
What’s behind the selected bytes starting from 0xEC offset? It’s the sequence of 5 keys used by the malware in the demonstration process to correctly decrypt 5 files. I have 5 keys and nothing else, the malware doesn’t specify the name of the files associated to the defined keys. To get the list of the 5 files I had to reverse the malware a little bit more, look here:
The idea is simple: it tries to apply the keys to every single compromised file. It stops the process when all the right candidate files are found. The malware has a complete list of the compromised files. How does he know what’s the right key?
As you can see, in order to pass the *key test*, the malware decrypts a little part of the candidate file only (bytes from 0x20 to 0x2F offset). The resulting 16 bytes of a valid candidate are:
4 bytes: unique string “CTB1”, it’s the same for every compromised file
4 bytes: number of bytes of the original file
4 bytes: number of bytes of the compromised file
4 bytes: fixed value 1
The first and last dword are used in the key check. In the end of all, there are two simple checks to get the connection between a candidate file and his key.
Now that the key has been found the malware is ready to restore the original file. This is done in two distinct steps, and it involves the entire file except the first initial 0x30 bytes.
DCE780 mov [ebp+var_8], eax DCE783 decrypt_next_block: DCE783 lea eax, [ebp+expandedKey] DCE789 push eax DCE78A push [ebp+var_4] ; Buffer of 16 bytes to decrypt DCE78D push [ebp+var_4] ; Save the result in the same buffer DCE790 call AESDecrypt ; Decrypt the current block DCE795 add [ebp+var_4], 10h ; Switch to the next block DCE799 add esp, 0Ch DCE79C dec [ebp+var_8] ; Update the number of block to decrypt DCE79F jnz short decrypt_next_block
Decryption is done in blocks of 32 bytes (16 from the file and 16 equals to 0x00). The last step consists in a Zlib decompression (the compression is done with level 3).
Now you have your original file back.
Conclusion: the CTB-Locker demonstration process works with some files only and the keys are all hardcoded inside HiddenInfo file, it’s impossible to restore other files following this method.
Curiosity satisfied, see you soon!



Why not create a tool for anyone who is not very practical decryption like me but who had the pc infected with CTB Locker? Thanks to those who want to respond.
Well, it’s not so simple as it seems and I don’t even know if it’s really possible to restore all the original files… I’m trying to get some more info about the malware, I’ll keep you update.
good start but there is no way to decrypt without the original key.
Yes, that’s the point of the post.
I am a professional photographer. A few weeks ago my computer was attacked by CTB-LOCKER the one with the black screen and code KEY. Proven Data Recovery has been able to identify the VARIENT of the virus I have. It is – RSA-2048 CTB-Locker encryption virus.
They want 2,600 for the decryption of 300 image files that this virus has encrypted on a SD CARD. The computer still reads close to 900mb of data on the card and I have been told by multiple sources that there is a chance my images are still there, but I have had no luck and it’s going to take me quite some time to come up with this money so in mean time I am exploring other options and learning more about computers and code than I would otherwise have never cared to.
It angers me to no end that people can actually even do this. That they can hurt total strangers in this away. Hurt their jobs. Effect their lives just for the sake of doing so and then dangle our data in front of us so we freak out and jump. I refuse to pay this RANSOM and it is frustrating to no end that the supposed GOOD GUYS want WAY THE HELL MORE!! It’s very backwards to me and does not seem right. It is almost impossible to get a simple strait answer from people in this area and there is a lot of double talk and I have bad a couple people remote access my computer and I see them try things even I have tried.
The files that are blocked were never on my hard drive. I didn’t even have time to make a hard copy. One moment they were find and the next they were encrypted. I have done 2 system restored and a factory restore and computer has updated protection but the files remain locked on my card.
Is there any effective decryption for CTB-LOCKER – RSA-2048 CTB-Locker encryption virus
What are the odds? Is it even worth saving all this money for these people? He did ID the variant. Even that came as a shock. It’s all I have to go on. Maybe, if you think you have a solution for me of course I would be willing to work put pay arrangement but I would need to see at lest SOME proof. Maybe do one or two that I can see. There are 300 on the card and I am really quite desperate for this material, or to be told convincingly and enough times that all hop is lost. I am not at that point yet.
Thanks for your time
Sincerely
Scott
Pingback: CTB-Locker - Security News
Thanks for the analysis!
If I got the encryption part right, the malware creates a master-private and a master-public key for the server and sends the master-private key (which is then destroyed on the infected machine) to its CC through TOR. This is in contrast to other crypto-ransomware that wait for the CC server to send the master-public key;
I was wondering what happens if the CC server is never reached (due to no accessibility to TOR for example):
– Does the malware keep trying to send the master-private key for ever
OR
– Since the transmission of the master-private key fails once, the malware stops trying to transmit it?
If it is the first, then does it mean that the master-private key may be recuperated from the memory?
That’s an interesting point indeed. Your idea about the key is reasonable but I’m not sure about the presence of the master key in memory right now. I’m still working on it and I hope to understand how things are really working as soon as possible.
hi zairon my computer has infected by ctb locker virus and i am unable to revcover my data which is very important i saw your progress here to get rid of this virus did you find any solution to counter this malware shit please help me i am giving you my email for your convenience goldenman_1989@hotmail.com
Sorry but I can’t help you, there’s no solution to the problem…
Pingback: Tools to cryptanalyze files encrypted by CTB-Locker? | DL-UAT
Pingback: Where to find a full analysis of the encryption scheme of CTB-Locker? | DL-UAT
Pingback: Is cryptanalysis of CTB-Locker possible? | DL-UAT
Pingback: Is cryptanalysis of CTB-Locker really impossible? | DL-UAT
Sir I need of Decrypt only 1 File
Plz Help
Sad to say but I can’t decrypt it…
who know that how to open my file from CTB Locker please help me
I was curious, so I got a sample from http://kernelmode.info. I ran it in a VirtualBox VM with networking disabled. After I copy-pasted the public key to a TOR browser outside the VM, the site allowed me to decrypt two (any) files for free. I uploaded an encrypted text file I created for this purpose, and the hidden server was able to decrypt my file. How could it do it when the malware was never able to communicate with the remote server?
How do you create the encrypted text file?
In a new WinXP VM, I created a file “important.txt” with the content “foobarbazbax123456789”. I then ran the malware sample I downloaded, which encrypted the files, including this TXT file, and gave me the public key and the link. I visited the link outside of the VM in TOR browser, they asked me for 1.65BTC, and allowed me to upload any two encrypted files to decrypt for free. I uploaded the encrypted “important.TXT.rgzifze”, and they were able to decrypt it, even though CBT-Locker was never able to reach the internet (I disabled it in VirtualBox).
There’s no need to access the internet when all the needed informations are secretly included inside the encrypted file. Take a look at my next blog post about CTB, there’s a full description of the real encryption/decryption scheme used by the malware.
Is there any decryption solution for ctb locker??
Hi dears any one please help me….
I need to decrypt my files..
it is very importent
it was encripted by CTB locker
Thanks
it is very very importent files
hi
how do i decrypt my files
hi all in my system all files are encrypted by CTB locker what i have do now please help me to remove this virus
hi all in my system all files are encrypted by CTB locker what i have do now please help me to remove this virus
ps help ctb locker.
my file are encrypted pls help????
When the virus was encrypted file, to restore skype ctblocker please add nick. We will help you recover them. Thanks.
If you can really help, why not public how can we do? Thanks
we need a tool to decrypt that 5 files then we can use that 5 files decrypted with another tool to compare original file with encrypted file, like panda anti ramsomeware, this tool need the original file
My name is Scott . I am a professional photographer from Michigan. On August 11, 2015 my computer was infiltrated by hackers utilizing an advanced and evolving hacking and data encryption program. It is not the only one of its kind, however the bad guys are continuing to invent new and more powerful ways to separate people and companies from the things they need the most. It is something that never should happen. It is wrong what these people do and they are doing it every day. They are doing it as I write this. They call it RANSOMWARE. It is a word I myself, a common computer user, had not hear of.
These programs go by different names. They all do about the same thing, which is to lock you out of your own computer and/or render files on your hard drive inaccessible to you and most people on the planet incidentally. It is a troublesome and disturbing new trend in cybercrime and I feel law enforcement and our government are NOT doing nearly enough to combat these people and their very REAL weapons.
They seem to be targeting at random. Individuals, Small businesses, and even law enforcement its self. There is a new shared danger in this fluid situation that is different from other computer virus programs in that even with the best protection the government has at its disposal there are people who know how to break in. Once one of these RANSOMWARE programs is able to upload onto your system you may never know it is there until it strikes. When it does, it is very fast and there is nothing you can do to stop it. Your file icons will flicker and disappear. You will see this happen as I did. The files will reappear, but in an encrypted format that MOST people will never break, it seems. You will need to know a lot about computer CODE and DECRYPTION.
If you start to see your files going away the only thing you can do is unplug your system from the wall or shit it immediately down as fast as u can. Just hit the button!! In some cases doing an immediate system restore and/or factory restore can assist in the recovery of files. It depends a lot on when your last hard drive RESTORE POINT was made. That is something you should often do, particularly if you do a lot of work on your computer and have more files you are dealing with.
The best thing you can do keep updated copies of important material. On CD as well as computer that is NOT connected at all to the internet. That is want I mostly do. I have computers for networking and I have other for editing and other things. It is best to keep things separate, now more than ever.
As of this writing there is no decryption for the version of this virus program that has locked my files from me. It is called CTB-LOCKER. It uses RSA-2048 ENCRYPION . Please feel free to google these things so you can learn more about what these programs really are, how they work and how dangerous they really are. Or google RANSOMWARE. I am hopeful that one day soon they will catch these evil people, or the good guys will come up with a solution. Some of these people have actually stopped and released their CODES so people could actually retrieve their data, but every situation is different and no one can say for sure if decryption will ever happen. I know there are a lot of people out there like me who have been victimized by these evil people and I want them to know that I feel their pain. I want to see these evil bad people in court. I want them to know that they have HURT PEOPLE and I want to see them go away for the rest of their lives.
I want to thank Roxy Lopez again for her courage in taking on this global issue and I thank here again for her time. Hopefully together we can get this very serious issue into a greater light and maybe the bad guys will have less places to hide.
Sincerely
Scott Matthew Smith
8-24-15
Pingback: A king’s ransom: an analysis of the CTB-locker ransomware | vulnerablelife
is there anyone who did decryption their files infected by CTB-Locker ? However, extention of my files are “.vaegran” thanks in advance.
Hi! very interesting post! I read that this malware, to decrypt a file, mixes 16 bytes of the encrypted file with 16 zeroes (appended at the end), but how does it work? I mean, what part of the result is taken, and how long is the result of this operation? Are zeroes appended in the encryption part as well? I wonder what are the mathematical consequenses of this…
helo , I have some family photos encrypted with ctb locker,
4MHKKEL-E5FAUUU-XJ7MOK3-CAWCZDU-ZRQJ3VY-EYPTJRD-AMWHYTB-IUYF6QN
PNZZUN2-3A7KI35-HZGZOJC-7FCICKD-BJLVTZY-IAVWD3F-VSYXCET-LS5C52G
7COW7EH-PB6S5DC-VMUDFMS-SANB5BJ-ZTSIVOA-MNIOEHQ-BHFYTTF-SIUYBZT,
http://regeotqlnafehgk7.onion/
bitcoin: 1GtcQUHczoUqpxvc5mVTn9TQgRAfPLPU1y
any solution for decrypt?
my email:geoneogeo35@gmail.com , help
If you haven’t used your computer very much since the infection, you could try a software such as recuva, photorec/testdisk or the like, because ctb locker creates an encrypted copy of the original file, than it deletes the original one, so there’s a chance to recover a few files with a sort of ‘undelete’ operation (though the result is unpredictable, I can’t tell you how many files you can recover, if any). As for decryption, that’s quite impossible.
Regards.
thanks for your info , i know about photorec,encase,r-studio, i didn’t manage to recover because i formatted my pc,that ransome 1500 usd is huge , some people like me gain in a mounth 250 euro, waiting for an ctb locker decryptor
Hallo All.
If I have the original and encrypted file is it possible to found the key?.
What i can’t understand: Why is so fast to copy files, encrypt and delete the original?
please send me 1-2 encrypted files in order to i can check and advice you if decryptable or not.
My Email Address: mcerdem82@yahoo.com
My spouse and I stumbled over here coming from a different web address and thought I may as well check things out. I like what I see so now i’m following you. Look forward to going over your web page again.
hi, i can help for recovery of arrow, java, arena, cezar and bip extension files, but please note that my service is not free (please contact me by mcerdem82@yahoo.com)
Right now it seems like Expression Engine is the best blogging platform available right now. (from what I’ve read) Is that what you’re using on your blog?
doctors in houston tx http://www.vogaisecompanhia.pt/anadrol-preзo-pfz.php best diet pills for fast weight loss